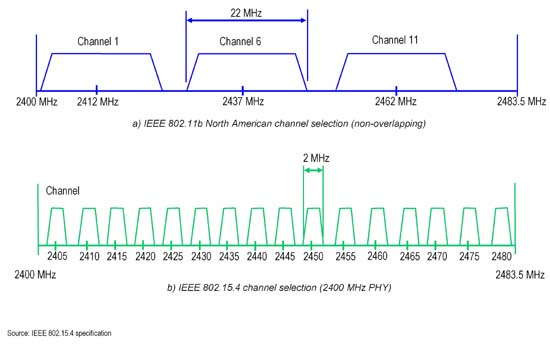
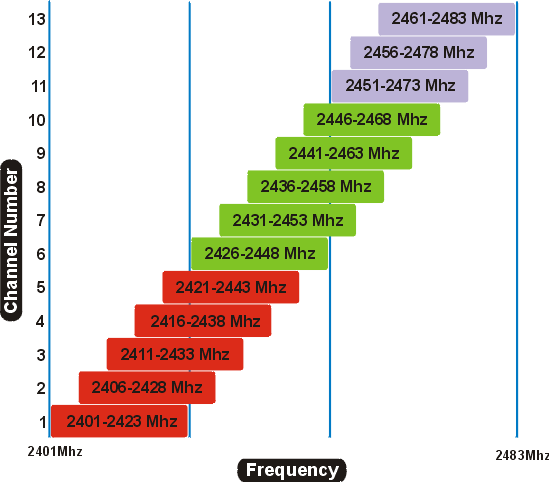
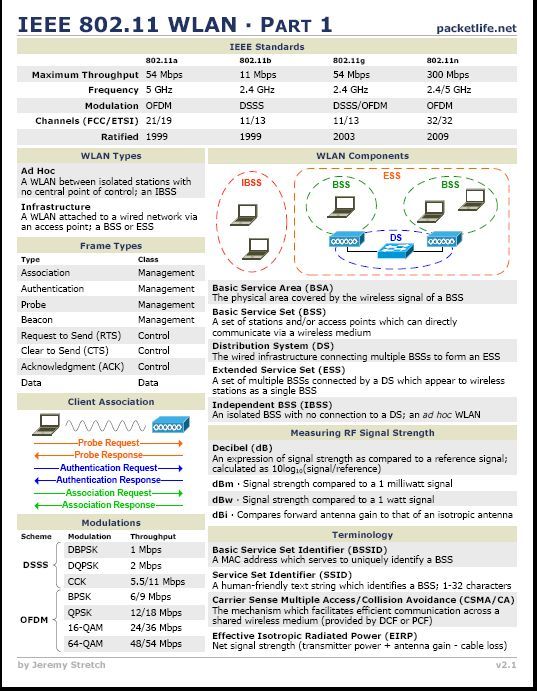
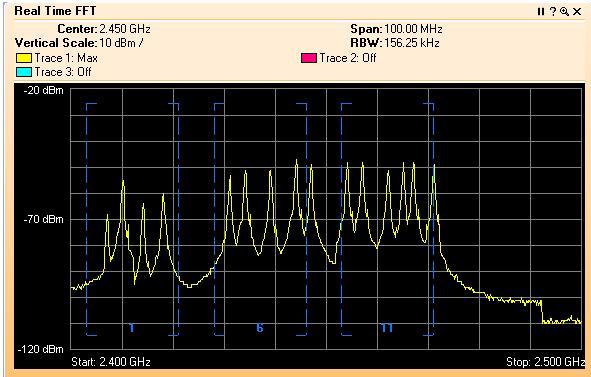
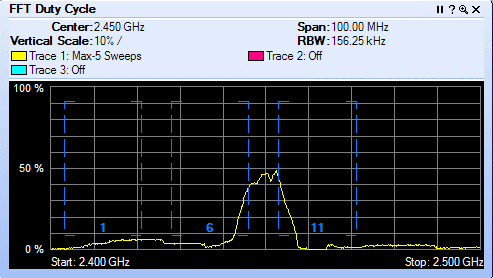
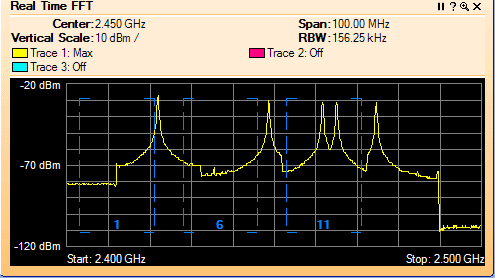
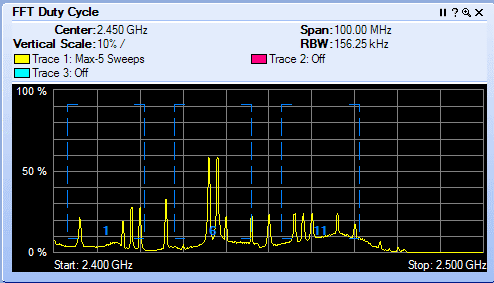
WFD#7 is a sponsored event that brings WiFi vendors also called sponsors and WiFi subject matter experts also called delegates together to discuss technology. WFD#7 sponsor list has returning vendors like Fluke AirMagnet, Wildpackets, AirTight, Aruba, Extreme Networks and Cisco. Avaya is a first time sponsor to WFD. Welcome!
I understand a few of the sponsors will be unveiling some exciting news. Only one way to learn about these unveilings first, tune into the live stream!
I’m interested in WFD newcomer Avaya. Avaya has been around since the early days when WiFi was just 802.11, no fancy task groups are the 11. They seem to have fallen by the way side in the early 2000’s. To date I can’t say I’ve seen their new WiFi solution in the wild. I’ve seen many customers using their communication suite of products. They have a nice suite that pulls together end to end communication and collaboration. Looking forward to learning more about their solutions.
Over the years and after many of the WFD events you build relationships with vendors.You collaborate together. You troubleshoot together. You test new widgets together. You share in successes together. Can’t wait to see my old friends at Wildpackets, Airmagnet, Cisco and Aruba.
Presentation Calendar
Most presentations are streamed live on this page, at TechFieldDay.com, and at some delegate and presenter web sites. After the event, the following pages contain video recordings of these presentations.
Wednesday, Aug 6 10:00-12:00
Fluke Networks Presents at Wireless Field Day 7
Wednesday, Aug 6 13:30-15:30
AirTight Networks Presents at Wireless Field Day 7
Wednesday, Aug 6 16:00-18:00
Extreme Networks Presents at Wireless Field Day 7
Thursday, Aug 7 8:00-10:00
Avaya Presents at Wireless Field Day 7
Thursday, Aug 7 10:30-12:30
Aruba Networks Presents at Wireless Field Day 7
Thursday, Aug 7 14:30-16:30
WildPackets Presents at Wireless Field Day 7
Friday, Aug 8 9:30-11:30
Cisco Presents at Wireless Field Day 7
WFD#7 delegates
http://techfieldday.com/event/wfd7/
Blake Krone @BlakeKrone
Blake Krone is Cisco CCIE Wireless and CWNA certified Wireless Network Architect with experience designing and deploying enterprise class networks supporting hundreds of APs and multiple controllers for Voice, Data, and RTLS.
Craig Schnarrs @The_WiFi_Guy
Craig Schnarrs, is senior wireless network operations engineer and WiFi blogger
George Stefanick @WirelesssGuru
George Stefanick is a Wireless Architect employed by a large healthcare system in the Texas Medical Center.
Glenn Cate @GRCate
Glenn Cate is a senior IT analyst who is passionate about all things Wi-Fi!
Jake Snyder @JSnyder81
Jake is a Systems Engineer focused on designing and deploying wireless networks in the Pacific Northwest.
Jennifer Huber @JenniferLucille
Jennifer has over 10 years of experience in the networking and wireless engineering industry.
Keith R. Parsons @KeithRParsons
Keith is Managing Director of Wireless LAN Professionals, and focuses his energy on providing great WLAN education, design and consulting to global customers.
Lee Badman @WiredNot
Lee Badman currently writes for Network Computing Magazine as Wireless and Mobility blogger, and has over twelve years of professional industry analysis under his belt.
Peter Paul Engelen @PPJM_Engelen
Peter-Paul Engelen is a technical consultant with advanced (pre) sales experience and business development skills in multi-vendor Cloud-based (W)LAN and Wholesale ISP/Carriers.
Richard McIntosh @CiscoTophat
Network engineer at a higher education institute with a focus in wireless networking.
Sam Clements @Samuel_Clements
Sam Clements is an avid wireless technologist with a passion for all things mobility.
Stewart Goumans @WirelessStew
Stewart is a Mobility Consultant helping customers and fellow WiFi'ers with wireless design in Vancouver British Columbia, Canada
Buckle in and get your WiFi on!
 Saturday, November 29, 2014 at 5:50PM
Saturday, November 29, 2014 at 5:50PM