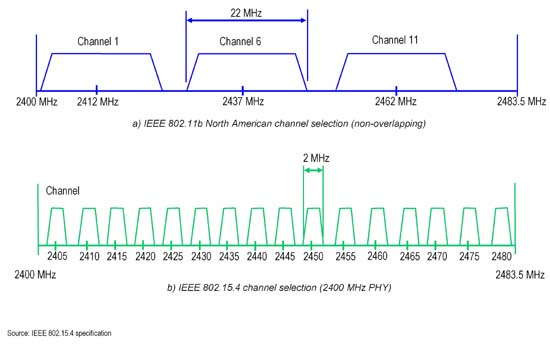
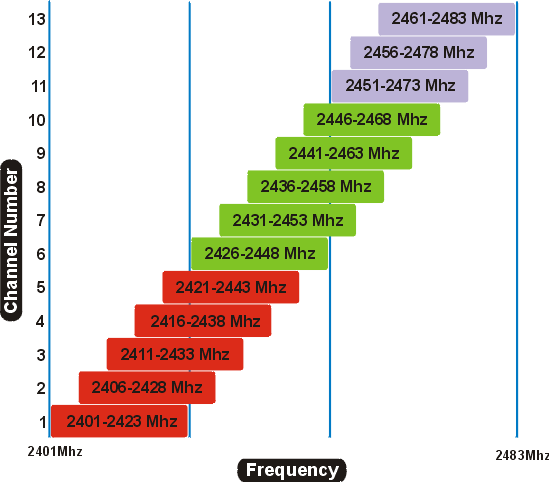
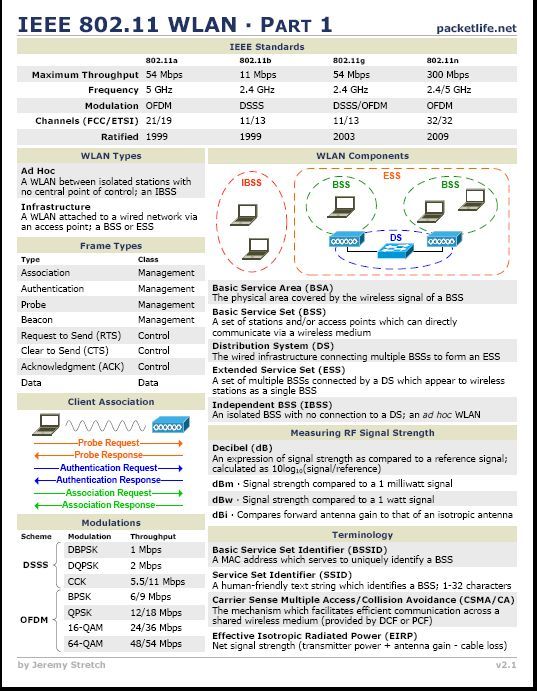
Wireless Tech Field Day Starts today @ San jose #WFD3
 Tuesday, September 11, 2012 at 3:18PM
Tuesday, September 11, 2012 at 3:18PM I am very humbled to be asked back to participate as a delegate in WFD3, presented and hosted by GESTALT IT. WFD3 <Wireless Field Day 3> brings some new vendors and new delegates together for yet another event filled wireless geek gathering. “ GESTALT IT Independent Experts United “
WFD is an event where industry users <experts in some cases> come together with wireless vendors to discuss wireless, technology road map and issues and features with the respected vendors. This allows vendors first hand experience with users who may be using their product already, whereby providing valuable feedback or in some cases introducing their product to users for the first time.
wireless, technology road map and issues and features with the respected vendors. This allows vendors first hand experience with users who may be using their product already, whereby providing valuable feedback or in some cases introducing their product to users for the first time.
WFD is also a large social media event. WFD has hundreds and sometimes thousands of like minded folks who will follow along and sometime paticpate in twitter feeds from each event.
This particular WFD3 brings together both hardware and software vendors.
Sponsoring Vendors
I would like to personally thank Aerohive, Aruba, Cisco, Meraki , Metageek and Ruckus for their repeated support and sponsorship of WFD. I would also like to thank and welcome Tabaza, Wildpackets and Juniper who are new sponsors.









WFD3 Delegates
WFD brings together like minded individuals who share common interest in technology, in the case of WFD, lets just say, it’s wireless geek week at its best! Each delegate brings a unique real world experience and perspective. Some delegates work for VARS, others are independent consultants or end users.
WFD3 delegate notables:
Blake Krone - CCIE Wireless
Keith Parsons - CWNE, Wifi Industry Expert and mentor to many of us
Gregor Vucanjnk - CWNE, Recently minted <like last week recent -CONGRATS>
Tom Carpenter - CWNP
Jennifer Huber - CWNE
Below are all attending delegates:
Vendor Questions and Perspective
As a wireless architect for a large and world renown healthcare system I will be focusing my questions and comments around healthcare specific WiFi. WiFi in healthcare presents very unique challenges. Real time applications requiring wire like connectivity and reliability. Large HC systems can have thousands of WiFi devices from COWs, mobile desktops, tablets, handhelds, scanners, RFID tags and the list goes on.
I am interested in how each hardware vendor is handling 802.11u, 802.11w, BYOD, MESH, 802.11ac, 802.11r and especially the APPLE explosion in Healthcare. These are hot buttons on my plate as well as many other Healthcare WiFi professionals.
- Healthcare is facing tighter budgets due to recent reform. Health Systems need to be cost aware when making purchases and get more bang for the buck. How are vendors positioning their product to compete in the current Healthcare market.
- BYOD and on boarding challenges and cost associated. Healthcare is leading the charge with BYOD. The sheer volume of WiFi devices contained within most hospital systems is larger than the population of some towns!
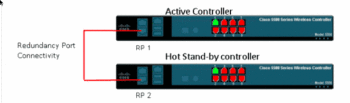
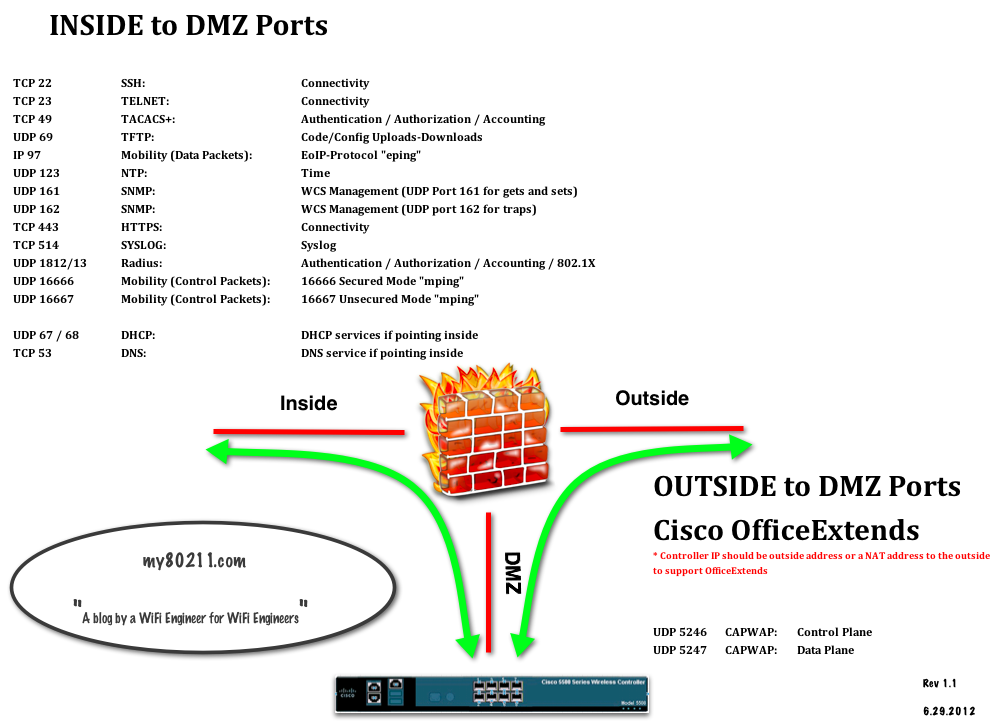
- How does Cisco’s new HA license and vWLC change the game ?
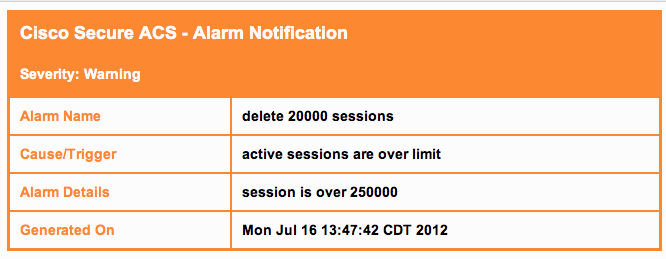
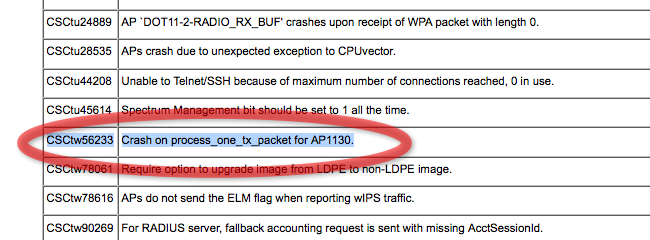
- Built in Rogue and wIPS systems - most are clunky and dont work well and have a cloud of mystery behind them.
- How are vendors supporting the APPLE explosion. Any new features or roadmap to better support troubleshooting and making up for APPLE deficiencies.
- Are vendors partnering with Apple to provider a better WiFi user experience. Looking for vendor perspective on the Apple road map, what are they doing with Apple to make our life easier
- PCI and HIPAA any new or existing features that allow admins to pull relevant data. Does this cost extra ?
- Vendors take on controller vs. controllerless platforms<We know where Aerohive stands :) >
- How secure is WiFi “cloud” computing - Vendor perspective?
- Remote Office Solutions - Vendor perspective ?
- 802.11ac roadmap
I am a BIG fan of Wildpackets. There is no better wireless sniffer in the world. Excited to meet the wildpackets team.
Never used Tanaza, very interested to hear about their offerings.
My friends, we are in a middle of a compelling wifi convergence. Never before has WiFi seen the attention or the publicity like it has in recent years. WiFi is a moving force like no other, you cant stop it nor can you contain it. Most of the population on planet earth knows what WiFi is. Just grab on and enjoy the ride!
WTD3 Schedule:
| Wed, Sep 12 | 15:00-17:00 | WildPackets Presents at Wireless Field Day 3 |
| Wed, Sep 12 | 16:30-17:00 | Dinner with Aerohive at Wireless Field Day 3 |
| Thu, Sep 13 | 08:00-10:00 | MetaGeek Presents at Wireless Field Day 3 |
| Thu, Sep 13 | 10:30-12:30 | Ruckus Presents at Wireless Field Day 3 |
| Thu, Sep 13 | 13:30-14:30 | Tanaza Presents at Wireless Field Day 3 |
| Thu, Sep 13 | 16:00-18:00 | Meraki Presents at Wireless Field Day 3 |
| Fri, Sep 14 | 08:00-12:00 | Aruba Presents at Wireless Field Day 3 |
| Fri, Sep 14 | 13:30-15:30 | Cisco Presents at Wireless Field Day 3 |
| Fri, Sep 14 | 16:00-18:00 |
WFD3 will be broadcasted LIVE at the following link at the above scheduled times:
http://techfieldday.com/event/wfd3/
EVENT STAFF
A big thank you to Stephen Foskett for putting up with "us" wireless geeks and hosting another great event!
| Benjamin Freedman | @PrimeImageBen | |
| Scott D. Lowe | @OtherScottLowe | |
| Scott Sexauer | ||
| Stephen Foskett | @SFoskett |