Top 10 Sessions From Interop Las Vegas 2015
 Friday, May 22, 2015 at 9:26AM
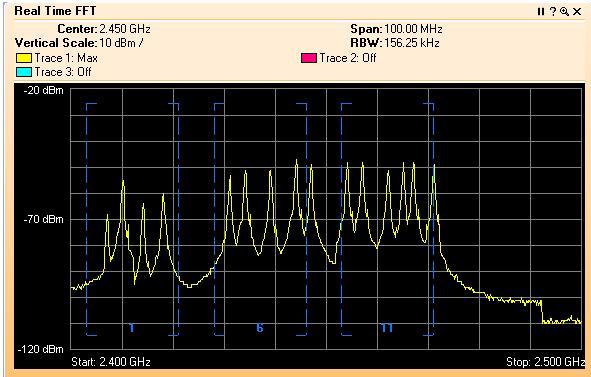
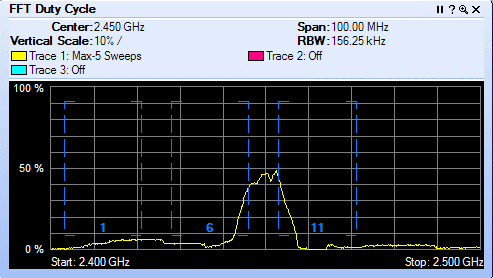
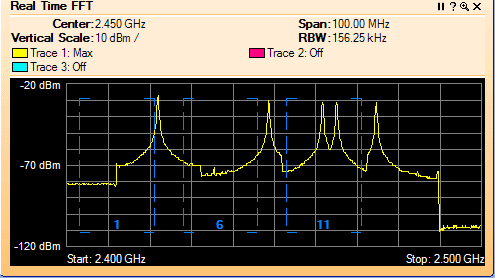
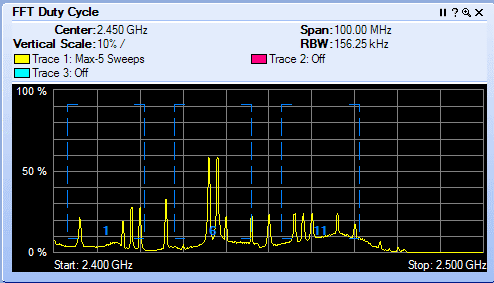
Friday, May 22, 2015 at 9:26AM Interop Las Vegas 2015 was a blast! Few conferences bring together a rich mix of vendors, products, solutions and attendees all in one place. I was particularly interested in Cisco's Hyperlocation, which just so happen to win Best of Interop Award - 2015 Mobility. Interop was a gathering of old friends and meeting new ones. I thought the mobility track was exceptional this year.
win Best of Interop Award - 2015 Mobility. Interop was a gathering of old friends and meeting new ones. I thought the mobility track was exceptional this year.
Cisco Hyperlocation:
http://www.interop.com/lasvegas/special-events/best-of-interop-awards.php?itc=we_ilv_le_ilv_drp_text
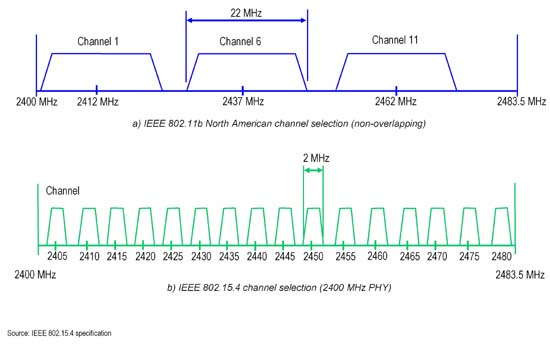
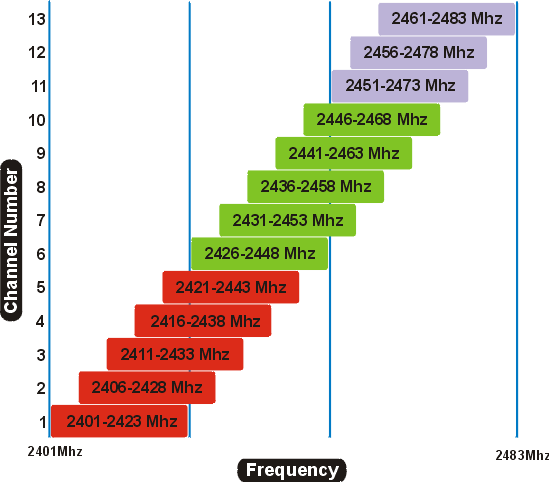
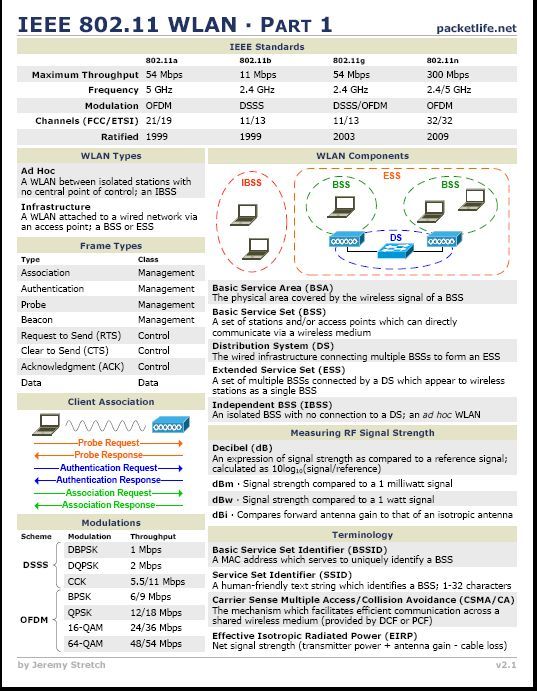
I was also a panel guest at Cisco's Mobility lunch where WiFi Mobility, 802.11ac and our AWO (All Wireless Office) was topic of discussion. It was 60 minutes of great discussion and guest interaction. I would like to thank Cisco's Bill Rubino for the invite.
I spoke at my own session "Designing Todays WiFi Network for Tomorrow's Applications". I always enjoy sharing my real world hands on experience with others. WiFi is still black magic to many IT folks in the industry. The goal in my session, take 2 things away that you didn't know before. I think the attendees agreed. My session made Interop's Top 10 Sessions and ranked #6 in the standings as voted by attendees. I would like to thank Andrew Murray for the invite and having me back at Interop.
Interop Top 10
http://www.informationweek.com/interop/top-10-sessions-from-interop-las-vegas/d/d-id/1320459?
In closing three articles were published from my Interop session.
Remember The Restroom When Deploying Wireless
What happens if you remove an acceptable use policy from guest Wi-Fi?
Diversity of connected devices in hospitals poses unique challenge for going fully wireless
Cheers!
 George |
George |  Post a Comment |
Post a Comment |