GEORGE STEFANICK - CWSP JOURNEY, (CHAPTER 4 –AAA, POST#8)- 2/11/2011
 Saturday, February 12, 2011 at 12:48AM
Saturday, February 12, 2011 at 12:48AM I’m back !!!!! On the study horse that is...
AAA – What is it ?
“Triple A”, as it is sometimes called, is a model for access control. It really is the model and basic frame work for security. There are 3 distinctive features in AAA, which are:
Authentication
Authorization
Accounting
Authentication
Authentication is the process to determine whether someone or something (entity) is, in fact, who they say they are. This is commonly done with user credentials (logon and password). The credentials are then presented to a “server” for verification. Other means, such as tokens and digital certificates can also be used in place of or combined with user credentials. This is called multi layer authentication. It is used to enhance the authentication process.
Authentication uses UDP port 1812, prior to IANA allocation 1645
Authorization
Once the entity is authenticated. Authorization can then take place. Authorization is the process of granting access or permissions to the entity. You are allowing the entity the privilege to do or have access to something on your network.
Accounting
Accounting is a means of keeping track of the entity, while on the network. This is often used by security to track what the entity did, how long they were on the network, what commands they may have entered, etc.
Accounting uses UDP port 1813, prior to IANA allocation 1646
Radius Server
The radius server is sometimes called the AAA server. This is because most common radius servers support all three functions. The Cisco ACS server is an example of such a device.
Other Radius Servers Include:
Juniper Steel Belted Radius
Microsoft IAS (Server 2003)
Microsoft NAP (Server 2008)
Free Radius
Configuration Notes
Speaking from experience (also noted on page 121) there are 2 common mistakes that happen often when setting up a radius server. One is using the wrong port numbers. Two is using the incorrect shared secret between the radius server and the authenticator. If you have issues in your initial setup, this is something you should check.
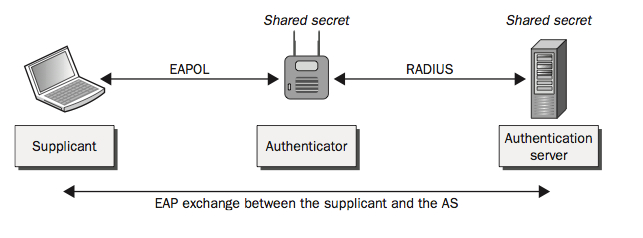
RFC
Radius Authentication and Authorization is defined in:
IETF RFC 2865
http://www.ietf.org/rfc/rfc2865.txt
Radius Accounting is defined in:
IETF RFC 2866
http://www.ietf.org/rfc/rfc2866.txt







Reader Comments