GEORGE STEFANICK - CWSP JOURNEY, (CHAPTER 5 – 4- WAY HANDSHAKE POST#5)- 10/03/2010
 Sunday, October 3, 2010 at 2:38PM
Sunday, October 3, 2010 at 2:38PM GEORGE STEFANICK - CWSP JOURNEY, (CHAPTER 5 – 4 WAY HANDSHAKE POST#5)- 10/03/2010
The 4-way handshake is a unique process and thus why I think it is important to cover in detail. But first lets recap.
We’ve learned the MSK (Master Session Key) is used for seeding material in the creation of the PMK (Pairwise Master Key) . The PMK (Pairwise Master Key) and GMK (Group Master Key) are then seeding material for the PTK (Pairwise Transient Key) and GTK (Group Temporal Key).
The MSK and PMK are negotiated between the supplicant and the authentication server (AAA). Once created, these keys are then moved to the authenticator (access point) via a Radius packet.
In contrast, PTK (Pairwise Transient Key) is derived differently. It is derived between the supplicant and the authenticator (access point). The authentication server (AAA), at this stage, has completed it’s task and is out of the mix.
Since the supplicant and the authenticator have mutual information about each other (PMK) key . They both can derive their unique Temporal keys in a process called the “4-way handshake” .
The purpose of the 4-way handshake is to derive a unique PTK key that will be used to encrypt client unicast traffic between this station and the access point. This key is unique. No two stations on an access point will have identical PTK keys.
So lets get started …
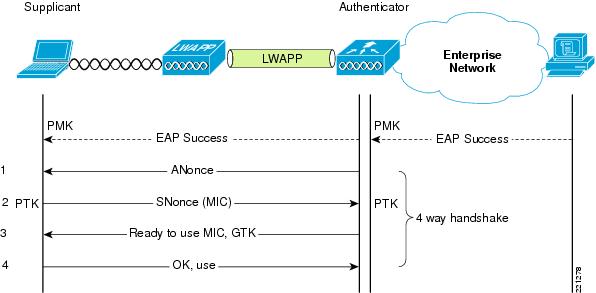
After a successful EAP authentication the 4-way handshake begins. Note, as I mentioned before, this is now between the supplicant and the authenticator.
The 4-way handshake shares very unique and random information between the supplicant and the access point to derive the PTK key. There is something called PRF (pseudo-random function). It uses a combination of “randomness”, as I like to call it.
It includes the PMK+ Supplicant Mac Address + Authenticator Mac Address + random Nonces) Here is the formula, it can be found on page 199 of the CWSP.
It’s a great visual …
PTK = PRF (PMK + ANonce + SNonce + AA + SPA )
Here are the definitions for reference:
PRF (pseudo-random function) - A collection of efficiently-computable functions which emulate a random oracle in the following way: no efficient algorithm can distinguish (with significant advantage) between a function chosen randomly from the PRF family and a random oracle (a function whose outputs are fixed completely at random). Pseudorandom functions are vital tools in the construction of cryptographic primitives, especially secure encryption schemes.
Nonce - is an abbreviation of number used once (it is similar in spirit to a nonce word). It is often a random or pseudo-random number issued in an authentication protocol to ensure that old communications cannot be reused in replay attacks.
ANonce – A authenticator nonce
SNonce – A supplicant nonce
AA – Authenticators Mac Address (access point)
SPA – Supplicants Mac Address (wireless client)
The 4-way handshake looks like a simple 4-way frame exchange. But inside these frames “random” magic is happening before your very eyes. Below is a breakdown of each exchange:
4-way handshake message 1
In the first message, the authenticator sends the supplicant a nonce. This is referred to as the ANonce. Along with this ANonce, the frame includes the authenticators mac address. At this point the supplicant has all the goods to create the PTK. It has the Anonce, authenticators mac address as well as its own Snonce and mac address, of itself.
4-way handshake message 2
The supplicant creates its nonce. This is referred to as the SNonce. The supplicant can now calculate the PTK because it has all the goods from the first handshake. In the second message, the supplicant sends the SNonce to the authenticator. The supplicant also sends the security parameters (RSN) information. The entire message gets an authentication check using the (KCK/MIC) from the pairwise key hierarchy. The authenticator can then verify that the information, including the security parameters sent at association are valid.
4-way handshake message 3
In the third message the authenticator derives the GTK key from the GMK key. The authenticator derives an ANonce, RSN information element info and a MIC. This information is then sent to the supplicant in a EAPOL-Key frame. This is kept secret from sniffing, because it is encrypted within the PTK.
4-way handshake message 4
The fourth message acts as a confirmation. It indicates that the temporal keys are installed.
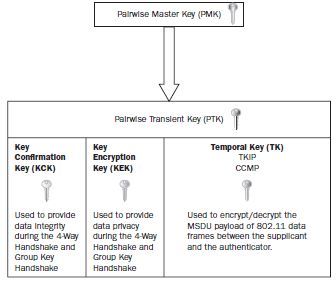
The PTK is comprised into three keys which is important to know, I like to call them the “internal PTK” keys. These KCK, KEK, and TK component. These keys secure the 4-way handshake (KCK), provide data integrity during the 4-way handshake (KCK) and provide encryption used to encrypt and decrypt the MSDU payload of 802.11 data frames between the station and the access point.
Key Confirmation Key (KCK) - The first key is the EAPOL-key confirmation key (KCK). The KCK is used by the EAPOL-key exchanges to provided data origin authenticity.
Key Encryption Key (KEK) - The second key is the EAPOL-key encryption key (KEK). The KEK is used by the EAPOL-key exchanges to provide for confidentiality.
Temporal Key (TK) - The third key is the temporal key, which is used by the data-confidentiality protocols (TKIP/CCMP)







Reader Comments (1)
Great post! Thanks buddy! Keep up this great work. Reading your blog has helped me better understand the 802.1X process.